|

|
Saturday, July 10, 2004
|
|
| |
----------------------------------------------------------------------
Boing Boing
----------------------------------------------------------------------
|
| 1. |
Old sci-fi rocket found at farm junk sale. A guy writes about finding an old beat-up rocket on a farm. It was made in the 1950 to promote the Rocky Jones TV show.
X-NAS-Bayes: #0: 1.60173E-082; #1: 1
X-NAS-Classification: 0
X-NAS-MessageID: 2893
X-NAS-Validation: {E681C936-E9F0-4DDC-9901-74301AF33E67}
 The farmer had hoped to restore the rocket but never got around to it. The child who won the rocket and his friends pretty much trashed the interior, the instruments are broken and the years of rain have rusted the rear bottom (near the fins) out. The shell body and doors are still amazingly strong and could be fixed without too much effort. The interior is in fantastic shape compared to the exterior. The owner has collected electrical equipment over the years, which can be seen in some of the shots, also he has new fluorescent lights for repairing the interior lighting. The farmer had hoped to restore the rocket but never got around to it. The child who won the rocket and his friends pretty much trashed the interior, the instruments are broken and the years of rain have rusted the rear bottom (near the fins) out. The shell body and doors are still amazingly strong and could be fixed without too much effort. The interior is in fantastic shape compared to the exterior. The owner has collected electrical equipment over the years, which can be seen in some of the shots, also he has new fluorescent lights for repairing the interior lighting.
Link (Thanks, Kirby Bartlett-Sloan!) |
----------------------------------------------------------------------
Yahoo! News - Technology
----------------------------------------------------------------------
|
| 2. |
Muscle Laptops (washingtonpost.com). washingtonpost.com - Laptop shoppers, relax: There's not a ton of innovation going on this year, and that's not necessarily a bad thing. |
----------------------------------------------------------------------
Slashdot
----------------------------------------------------------------------
|
| 3. |
Incorporating Machine Learning into Firefox 2.0? |
----------------------------------------------------------------------
NewsIsFree: Security
----------------------------------------------------------------------
|
| 4. |
Symantec Opens Its Security Center (PC World) |
| 5. |
Sun Microsystems Solaris dmi_cmd Malformed DB Entry dmispd DoS |
11:29:27 PM 
|
|
----------------------------------------------------------------------
Slashdot
----------------------------------------------------------------------
|
| 1. |
Modular Laser Launch Systems |
10:29:07 PM 
|
|
9:28:48 PM 
|
|
----------------------------------------------------------------------
Slashdot
----------------------------------------------------------------------
|
| 1. |
Carnegie Mellon Starts Offering Courses Online |
----------------------------------------------------------------------
SecurityFocus Vulns
----------------------------------------------------------------------
|
| 2. |
Vulns: Microsoft Windows Program Group Converter Filename Local Buffer Overrun Vulnerability. Microsoft Windows Program Group Converter (grpconv.exe) is an application that is used to convert Windows 3.1 groups to folders while upgrading from Windows 3.1.
X-NAS-Bayes: #0: 2.46294E-017; #1: 1
X-NAS-Classification: 0
X-NAS-MessageID: 2890
X-NAS-Validation: {E681C936-E9F0-4DDC-9901-74301AF33E67}
Microso... |
8:28:27 PM 
|
|
7:28:08 PM 
|
|
6:27:48 PM 
|
|
5:27:28 PM 
|
|
----------------------------------------------------------------------
Slashdot
----------------------------------------------------------------------
|
| 1. |
How To Make Friends on the Telephone |
----------------------------------------------------------------------
SecurityFocus Vulns
----------------------------------------------------------------------
|
| 2. |
Vulns: NPDS BB HTML Injection Vulnerability. NPDS BB is forum software written in PHP.
X-NAS-Bayes: #0: 5.37241E-049; #1: 1
X-NAS-Classification: 0
X-NAS-MessageID: 2886
X-NAS-Validation: {E681C936-E9F0-4DDC-9901-74301AF33E67}
A vulnerability is reported in the software that may allow a remote attacker to execute HTML and script code in a user's browse... |
----------------------------------------------------------------------
NewsIsFree: Security
----------------------------------------------------------------------
|
| 3. |
BugTraq: Covert Channels allow Cross-Site-Java in Microsoft VM |
----------------------------------------------------------------------
About Internet/Network Security
----------------------------------------------------------------------
|
| 4. |
Quick Tip: Configure Windows XP To Erase Page File. Windows uses a portion of the hard drive as virtual memory to supplement the RAM memory and allow more programs to run and windows to be open at the same time. The information is written to a page file which... |
4:27:08 PM 
|
|
----------------------------------------------------------------------
Yahoo! News - Technology
----------------------------------------------------------------------
|
| 1. |
Mozilla Gains on IE (PC World). PC World - Study shows Microsoft has lost a percentage of market share to open source browser. |
----------------------------------------------------------------------
Slashdot
----------------------------------------------------------------------
|
| 2. |
Too Few American Scientists? Maybe Not |
----------------------------------------------------------------------
SecurityFocus Vulns
----------------------------------------------------------------------
|
| 3. |
BugTraq: Covert Channels allow Cross-Site-Java in Microsoft VM. Sender: Marc Schoenefeld [schonef at uni-muenster dot de] |
----------------------------------------------------------------------
About Internet/Network Security
----------------------------------------------------------------------
|
| 4. |
Internet Explorer Users Beware. On the same day that Microsoft released their Security Bulletins for the month of June, security firm Secunia released an Advisory for two "extremely critical" vulnerabilities in Internet Explorer that aren't addressed by Microsoft yet. One vulnerability can be used... |
3:26:47 PM 
|
|
----------------------------------------------------------------------
Boing Boing
----------------------------------------------------------------------
|
| 1. |
Don't call him chicken. Sunjit Kumar of Suva, Fiji, was raised by chickens. As a young boy, his grandfather locked him in a chicken coop where he lived for several years. After Kumar escaped, he was taken to an old age home where the baffled staff confined him for twenty years. Now though, Elizabeth Clayton, president of a Rotary Club in Fiji's capital city, has, er, taken Kumar under her wing.
X-NAS-Bayes: #0: 1.26263E-172; #1: 1
X-NAS-Classification: 0
X-NAS-MessageID: 2884
X-NAS-Validation: {E681C936-E9F0-4DDC-9901-74301AF33E67}
"Sujit would mostly hop around like a chicken, peck at his food, perch like a chicken and make noises like a chicken," she said. "He would prefer to roost on the floor to go to sleep rather than sleep in a bed."
Kumar currently resides in a former factory while undergoing therapy. Video available here. More of the story here. |
----------------------------------------------------------------------
Yahoo! News - Technology
----------------------------------------------------------------------
|
| 2. |
Isn't Now the Time to Try a Linux Desktop? (Ziff Davis). Ziff Davis - Opinion: The crackers currently have the whip hand over Windows, and Microsoft's assertion that Internet Explorer is now part of the operating system shows its flawed reasoning. |
----------------------------------------------------------------------
Slashdot
----------------------------------------------------------------------
|
| 3. |
Homebrew Game & Watch Games Make Debut |
----------------------------------------------------------------------
SecurityFocus Vulns
----------------------------------------------------------------------
|
| 4. |
Vulns: DiamondCS Process Guard Service Description Table Restoration Vulnerability. DiamondCS Process Guard is a security system that protects both system and security processes from attacks by other processes. Process Guard accomplishes this functionali... |
| 5. |
Vulns: Comersus Open Technologies Comersus Cart Multiple Vulnerabilities. Comersus Cart is an e-commerce shopping cart application. It is written in ASP.
Comersus Cart is reported prone to multiple vulnerabilities. These issues may allow a r... |
| 6. |
Vulns: Enterasys XSR Security Router Record Route Denial Of Service Vulnerability. Enterasys XSR Security Routers are hardware routers with firewall, VPN, and standard router capabilities built in.
Enterasys XSR Security Routers are reported prone to a... |
----------------------------------------------------------------------
NewsIsFree: Security
----------------------------------------------------------------------
|
| 7. |
Norton Anti-Virus New Denial of Service (DoS) Vulnerability |
| 8. |
Hey - You Can Even Send Viruses from Word! |
----------------------------------------------------------------------
About Internet/Network Security
----------------------------------------------------------------------
|
| 9. |
Quick Tip: Configure Windows XP To Erase Page File. Windows uses a portion of the hard drive as virtual memory to supplement the RAM memory and allow more programs to run and windows to be open at the same time. The information is written to a page file which... |
2:26:27 PM 
|
|
----------------------------------------------------------------------
Ars Technica
----------------------------------------------------------------------
|
| 1. |
Ask Ars: FSB and memory speeds. Confused about what the FSB is and how fast your RAM is? Ask Ars clears up the mystery. By Eric Bangeman. |
----------------------------------------------------------------------
Slashdot
----------------------------------------------------------------------
|
| 2. |
Entropy Project Closes Up Shop |
----------------------------------------------------------------------
NewsIsFree: Security
----------------------------------------------------------------------
|
| 3. |
CMySQL 4.1/5.0 zero-length password auth. bypass Exploit |
1:26:07 PM 
|
|
----------------------------------------------------------------------
Yahoo! News - Technology
----------------------------------------------------------------------
|
| 1. |
The Rightness Of Lightness (washingtonpost.com). washingtonpost.com - The laptop computer business is doing better than ever, but the idea of the laptop computer is getting scrambled in the process. |
----------------------------------------------------------------------
Slashdot
----------------------------------------------------------------------
|
| 2. |
Commercial DVD Software Comes to Linux |
----------------------------------------------------------------------
SecurityFocus Vulns
----------------------------------------------------------------------
|
| 3. |
Vulns: Mbedthis Software AppWeb HTTP Server Multiple Vulnerabilities. Mbedthis Software AppWeb HTTP Server is an embedded Web Server solution.
X-NAS-Bayes: #0: 7.69266E-068; #1: 1
X-NAS-Classification: 0
X-NAS-MessageID: 2882
X-NAS-Validation: {E681C936-E9F0-4DDC-9901-74301AF33E67}
Mbedthis Software AppWeb HTTP Server is reported prone to multiple vulnerabilities that may all... |
| 4. |
Vulns: Network Time Protocol Daemon Integer Overflow Vulnerability. Network Time Protocol (NTP) is used to synchronize the clocks of computers over a network. The service can be used by client machines to synchronize the local date and t... |
12:25:48 PM 
|
|
----------------------------------------------------------------------
Yahoo! News - Technology
----------------------------------------------------------------------
|
| 1. |
Isn't Now the Time to Try a Linux Desktop? (Ziff Davis). Ziff Davis - Opinion: The crackers currently have the whip hand over Windows, and Microsoft's assertion that Internet Explorer is now part of the operating system shows its flawed reasoning. |
----------------------------------------------------------------------
Slashdot
----------------------------------------------------------------------
|
| 2. |
Mozilla Gains on Internet Explorer |
----------------------------------------------------------------------
SecurityFocus Vulns
----------------------------------------------------------------------
|
| 3. |
Vulns: Linux Kernel HbaApiNode Improper File Permissions Denial of Service Vulnerability. A vulnerability has been identified in the SuSE Linux kernel that may allow a local attacker to cause a denial of service condition on a vulnerable system. The issue is ... |
| 4. |
Vulns: Tripwire Email Reporting Format String Vulnerability. Tripwire is a change monitoring an reporting tool available for Linux and Microsoft Windows. It is commonly implemented to carry out intrusion detection, integrity assur... |
10:25:08 AM 
|
|
----------------------------------------------------------------------
Yahoo! News - Technology
----------------------------------------------------------------------
|
| 1. |
Apple Reinvention Transforms Stock Value (Reuters). Reuters - The more than 50 percent rise in
Apple Computer Inc.'s stock price this year has mirrored the
brisk sales of its market-leading iPod digital music player and
growth at its retail stores. |
| 2. |
Schools Debate Price of PCs and Corporate Altruism (Reuters). Reuters - A pilot project in Africa that
aims to provide a single computer that can be used by four
students simultaneously has stumbled across one of the business
world's basic facts of life. |
----------------------------------------------------------------------
Slashdot
----------------------------------------------------------------------
|
| 3. |
XORP 1.0 Released |
----------------------------------------------------------------------
NewsIsFree: Security
----------------------------------------------------------------------
|
| 4. |
wvWare Library Buffer Overflow Lets Remote Users Execute Arbitrary Code |
9:24:51 AM 
|
|
8:24:27 AM 
|
|
----------------------------------------------------------------------
Boing Boing
----------------------------------------------------------------------
|
| 1. |
DMCA says you can't fix your own tape-drive. My cow-orker Jason Schultz reports on a breaking new DMCA horripilation: a court has ordered a company to stop fixing tape-drives because in so doing, it makes unauthorized access of a copyrighted "Maintenance Code."
X-NAS-Bayes: #0: 4.22988E-129; #1: 1
X-NAS-Classification: 0
X-NAS-MessageID: 2859
X-NAS-Validation: {E681C936-E9F0-4DDC-9901-74301AF33E67}
A district court in Boston has used the DMCA to grant a preliminary injunction against a third party service vendor who tried to fix StorageTek tape library backup systems for legitimate purchasers of the system.
How is this a DMCA violation? Well, it turns out that StorageTek allegedly uses some kind of algorithmic "key" to control access to its "Maintenance Code", the module that allows the service tech to debug the storage system. The court found that third party service techs who used the key without StorageTek's permission "circumvented" to gain access to the copyrighted code in violation of the DMCA, even though they had the explicit permission of the purchasers to fix their machines.
Link |
| 2. |
Cancer causes visualised as a subway map. 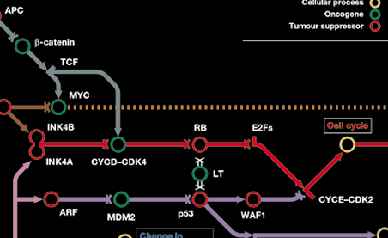
This is a really cool visualisation of the causes of cancer from Nature magazine, in which a faux subway map is dotted with cell types required for malignancy that are joined by the molecular pathways that generate these behaviours.
Link
|
| 3. |
Sf stories written to submitted images. Chris sez, "SciFiMage, a new section in Ultraverse, takes a unique approach story-telling. Instead of the editor -- that's me -- writing a story and then soliciting an artist to illustrate it, I take a submitted image and write a story about it. Anyone may submit an image -- one of their own, or someone else's."
Link
(Thanks, Chris!) |
----------------------------------------------------------------------
Yahoo! News - Technology
----------------------------------------------------------------------
|
| 4. |
Briefs filed in Oracle trial (SiliconValley.com). SiliconValley.com - A week after testimony ended in the Oracle antitrust trial, both sides marshaled evidence for their answer to the main question in the case: How many players are there in the market for high-end business-application software? |
----------------------------------------------------------------------
The Register
----------------------------------------------------------------------
|
| 5. |
Grassroots hackers create file-swapping wireless iPod. It's more of a bugfix, really |
----------------------------------------------------------------------
NewsIsFree: Security
----------------------------------------------------------------------
|
| 6. |
Silver Str: Frank Swiderski talks about his Threat Modeling Tool [Video] |
| 7. |
The Register: Computer Security - a handbook for the ordinary user "Written with home users in m... |
7:24:07 AM 
|
|
----------------------------------------------------------------------
Slashdot
----------------------------------------------------------------------
|
| 1. |
ARM: The Non-Evil Monopolist |
----------------------------------------------------------------------
Wired News
----------------------------------------------------------------------
|
| 2. |
Hybrid Tries to Escape SUV Stigma. Ford is ready to unleash a new species of car, the SUV hybrid, in September. While the Escape is designed with greens in mind, there are other reasons folks don't take kindly to SUVs. By John Gartner. |
| 3. |
Self-Taught Pilot Going to Space. Wild Fire -- a manned spacecraft made by volunteers for less than $4 million -- is eyeing a September launch date to propel passengers 70 miles above Earth's surface. If successful, developers are in line to win $10 million. By Dan Brekke. |
----------------------------------------------------------------------
NewsIsFree: Security
----------------------------------------------------------------------
|
| 4. |
E-Mail Security Puts PGP In Spotlight (TechWeb) |
| 5. |
Mozilla Patches Security Hole |
6:23:47 AM 
|
|
5:23:27 AM 
|
|
----------------------------------------------------------------------
Dilbert
----------------------------------------------------------------------
|
| 1. |
Dilbert for 10 Jul 2004.  |
----------------------------------------------------------------------
BBC News | Technology | UK Edition
----------------------------------------------------------------------
|
| 2. |
Playing war with the US army. As military-style video games become more lifelike, are they blurring the line between fantasy and reality? |
----------------------------------------------------------------------
Yahoo! News - Technology
----------------------------------------------------------------------
|
| 3. |
Oracle: Justice Failed To Make Its Case (TechWeb). TechWeb - Software vendor says in a filing that the government didn't prove its proposed acquisition of PeopleSoft would reduce competition. The Justice Department, however, cites substantial anti-competitive effects from an acquisition. |
4:23:07 AM 
|
|
----------------------------------------------------------------------
Slashdot
----------------------------------------------------------------------
|
| 1. |
Nursing Homes Go High-Tech |
----------------------------------------------------------------------
NewsIsFree: Security
----------------------------------------------------------------------
|
| 2. |
More Security Holes News... |
3:22:47 AM 
|
|
2:22:29 AM 
|
|
1:22:07 AM 
|
|
----------------------------------------------------------------------
Yahoo! News - Technology
----------------------------------------------------------------------
|
| 1. |
Amazon to Take Pre-Orders for Portable Media Center (Reuters). Reuters - Microsoft Corp. (MSFT.O) said on
Thursday that online Web shopping site Amazon.com Inc. (AMZN.O)
will begin taking orders for Portable Media Centers, a new line
of portable devices for listening to music and viewing video
content. |
----------------------------------------------------------------------
Slashdot
----------------------------------------------------------------------
|
| 2. |
Americans Read Fewer Books |
12:29:17 AM 
|
|
|

|
© Copyright
2004
Gregg Doherty.
Last update:
7/26/2004; 12:30:19 AM.
This theme is based on the SoundWaves
(blue) Manila theme. |
|
|

